At Experion, we’ve mastered Identity and Access Management (IAM), delivering custom, ironclad solutions that protect businesses globally.
Identity and Access Management (IAM) plays a vital role in cybersecurity by ensuring that authorized users can access the necessary resources at the right time. By efficiently managing user identities and controlling access, organizations can greatly reduce the chances of unauthorized entry, data breaches, and other security threats.
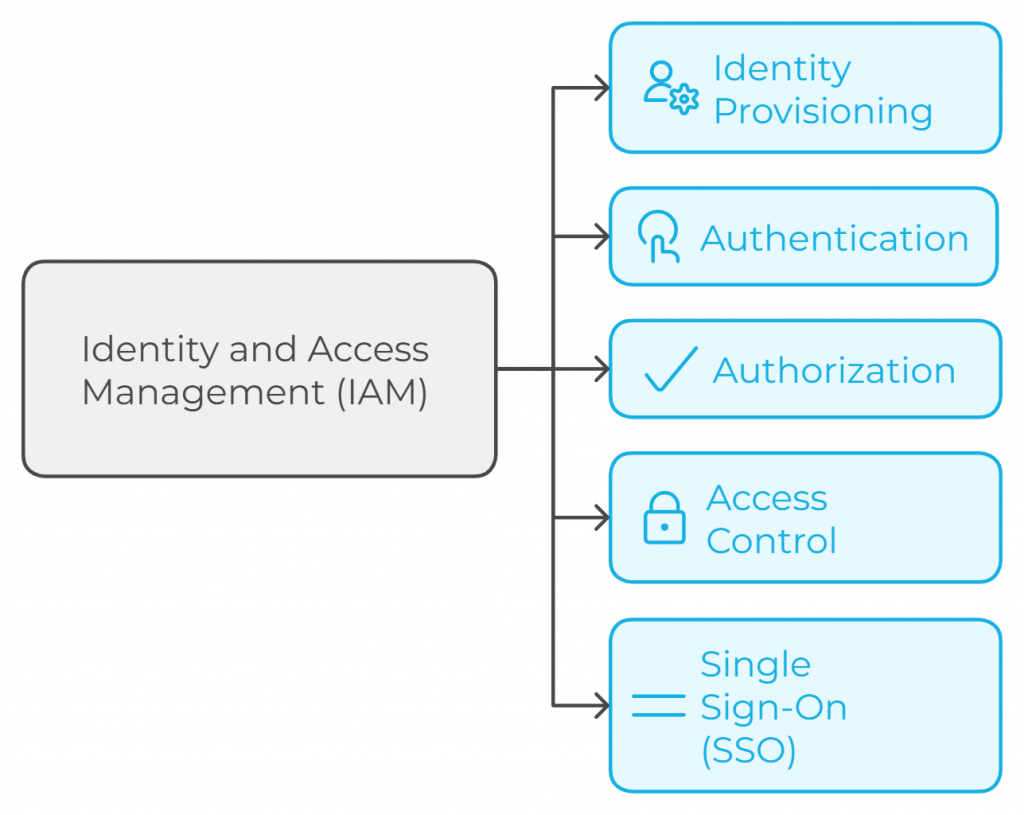
- Identity Provisioning: Creating and managing user accounts based on roles and responsibilities.
- Authentication: Verifying the identity of users through various methods, such as passwords, biometrics, or tokens.
- Authorization: Granting users specific permissions to access resources based on their roles and responsibilities.
- Access Control: Enforcing policies and procedures to restrict access to sensitive information and systems.
- Single Sign-On (SSO): Allowing users to log in to multiple applications with a single/same set of credentials.
Benefits of IAM:
- Strengthened Security: IAM ensures that only authorized personnel can access critical systems and sensitive data, helping to prevent unauthorized entry.
- Greater Efficiency: Features like single sign-on (SSO) simplify the login process by making it faster and easier for users while reducing administrative tasks.
- Regulatory Compliance: IAM aids businesses in adhering to important regulations and standards, such as GDPR, HIPAA, and PCI DSS.
- Lowered Risk: Implementing strong IAM practices helps minimize the likelihood of data breaches and other security threats.
Experion’s IAM Solutions
At Experion, we offer comprehensive IAM solutions to help organizations protect their valuable assets. Our services include:
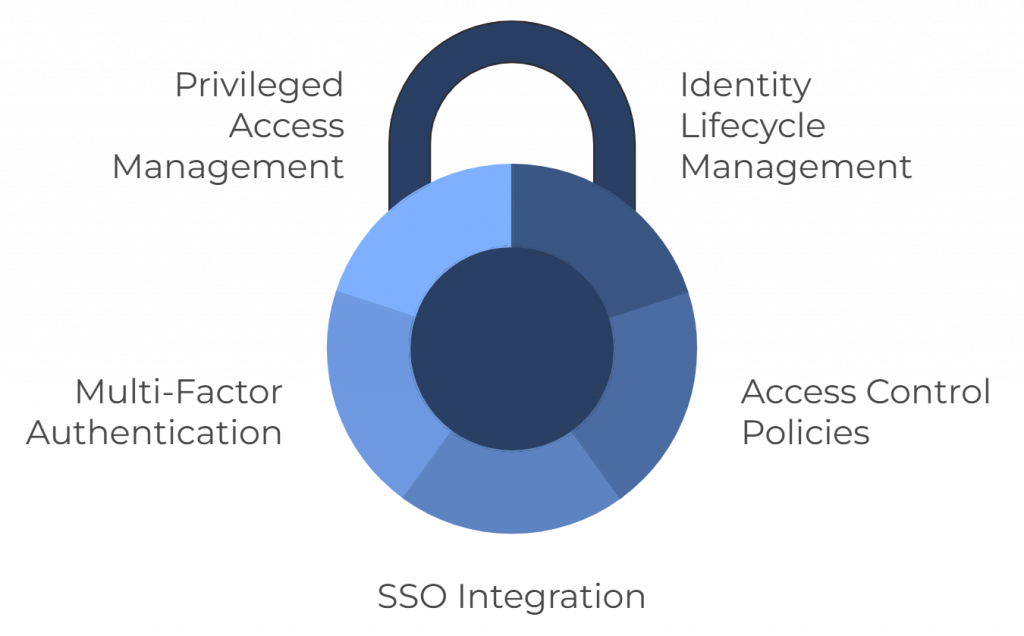
- Identity Lifecycle Management: Overseeing every stage of user identity management, from creation to removal.
- Access Control Policies: Establishing strong access control measures to protect sensitive data by limiting access.
- Single Sign-On (SSO) Integration: Simplifying user authentication by implementing SSO for seamless login experiences.
- Multi-Factor Authentication (MFA): Enhancing security by adding an additional layer of authentication beyond just passwords.
- Privileged Access Management (PAM): Managing and securing privileged accounts with higher-level access to ensure strict control.
Beyond the Basics: Advanced IAM Considerations
While the core components of IAM are essential, organizations must also consider more advanced factors to ensure comprehensive protection:
- Risk-Based Access Control: Implementing policies that grant access based on risk factors, such as user behavior and location.
- Continuous Monitoring: Continuously monitoring user activity and access patterns to identify potential security threats.
- Adaptive Authentication: Using context-aware authentication methods that adjust based on factors like user behavior, location, and device.
- Data Privacy: Ensuring that IAM practices align with data privacy regulations and protect personal information.
- Integration with Other Security Tools: Integrating IAM with other security tools, such as firewalls, intrusion detection systems, and encryption solutions, to create a comprehensive security framework.
By partnering with Experion for your IAM needs, you can ensure that your organization’s sensitive data is protected, and your employees can access the resources they need to be productive. Our experts will work with you to develop a customized IAM solution that meets your specific requirements and helps you achieve your business goals.
Conclusion
As digital landscapes expand and threats evolve, the importance of Identity and Access Management (IAM) becomes increasingly clear. IAM is no longer just about controlling who gets in—it’s about protecting what matters most to your business. By ensuring the right individuals have access to the right resources at the right time, organizations can maintain security without sacrificing productivity. Whether you’re scaling operations or safeguarding sensitive data, a well-implemented IAM strategy offers the foundation needed for secure, streamlined digital growth. It’s not just about staying safe—it’s about staying ahead.
Experion’s IAM services not only enhance security but also streamline user experience and ensure compliance. Ready to fortify your digital front door? Let Experion’s cybersecurity experts lock it down with confidence.

