At Experion, we protect what matters most. With years of expertise in delivering robust cybersecurity solutions for hundreds of businesses worldwide, we ensure that your data and systems are always secure.
Information security is a crucial component of cybersecurity, with a primary focus on safeguarding sensitive data and digital assets from unauthorized access or breaches. It encompasses the protection of both digital and physical information across various platforms and systems. While cybersecurity encompasses the broader protection of computer systems and networks, information security delves into the confidentiality, integrity, and availability of sensitive data.
Key Concepts in Information Security
- Confidentiality: Protects information by making it accessible only to authorized individuals. It aims to prevent unauthorized access, disclosure, or interception of sensitive data.
- Integrity: Ensures data remains accurate and complete, safeguarding it from unauthorized changes, alterations, or deletions.
- Availability: Guarantees that authorized users have access to information when needed, by minimizing disruptions that could interfere with access to services or systems.

Common Threats to Information Security
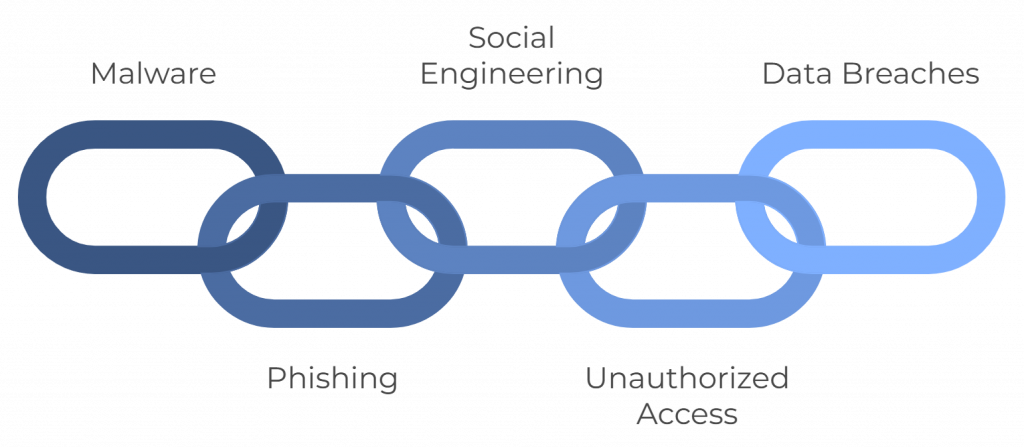
- Malware: Malicious software such as viruses, worms, and trojans that can compromise system security and steal or damage data.
- Phishing: Attempts to deceive individuals into revealing sensitive information through fraudulent emails or websites.
- Social Engineering: Manipulating individuals into divulging confidential information or performing actions that compromise security.
- Unauthorized Access: Gaining access to systems or data without proper authorization, often through hacking or exploiting vulnerabilities.
- Data Breaches: Incidents where sensitive information is exposed to unauthorized individuals, leading to potential financial loss, reputational damage, and legal consequences.
Information Security Measures
To protect against these threats, organizations implement a variety of security measures, including:
- Access Controls: Restricting access to systems and data based on user roles and permissions.
- Encryption: Transforming data into a code that can only be decrypted by authorized parties.
- Firewalls: Network security devices that filter incoming and outgoing traffic to block unauthorized access.
- Intrusion Detection Systems (IDS): Monitoring networks and systems for signs of unauthorized activity or attacks.
- Security Awareness Training: Equips employees with the knowledge of security best practices and teaches them how to identify and avoid threats such as phishing and social engineering.
- Incident Response Planning: Establishes a structured plan to address and mitigate security breaches, reducing potential damage and ensuring a swift recovery.
Information Security as a Service: Experion’s Approach
At Experion, we understand that safeguarding your organization’s sensitive data is paramount. That’s why we offer comprehensive Information Security as a Service (ISaaS) solutions tailored to your specific needs.
Our ISaaS offerings include:
- Threat Assessment and Risk Management: Our experts thoroughly assess vulnerabilities and craft effective strategies to mitigate risks.
- Security Awareness Training: We offer engaging training programs to educate your team on security best practices, helping them identify and avoid threats like phishing and social engineering.
- Incident Response Planning: We assist in building and implementing comprehensive incident response plans to swiftly manage and minimize the impact of security breaches.
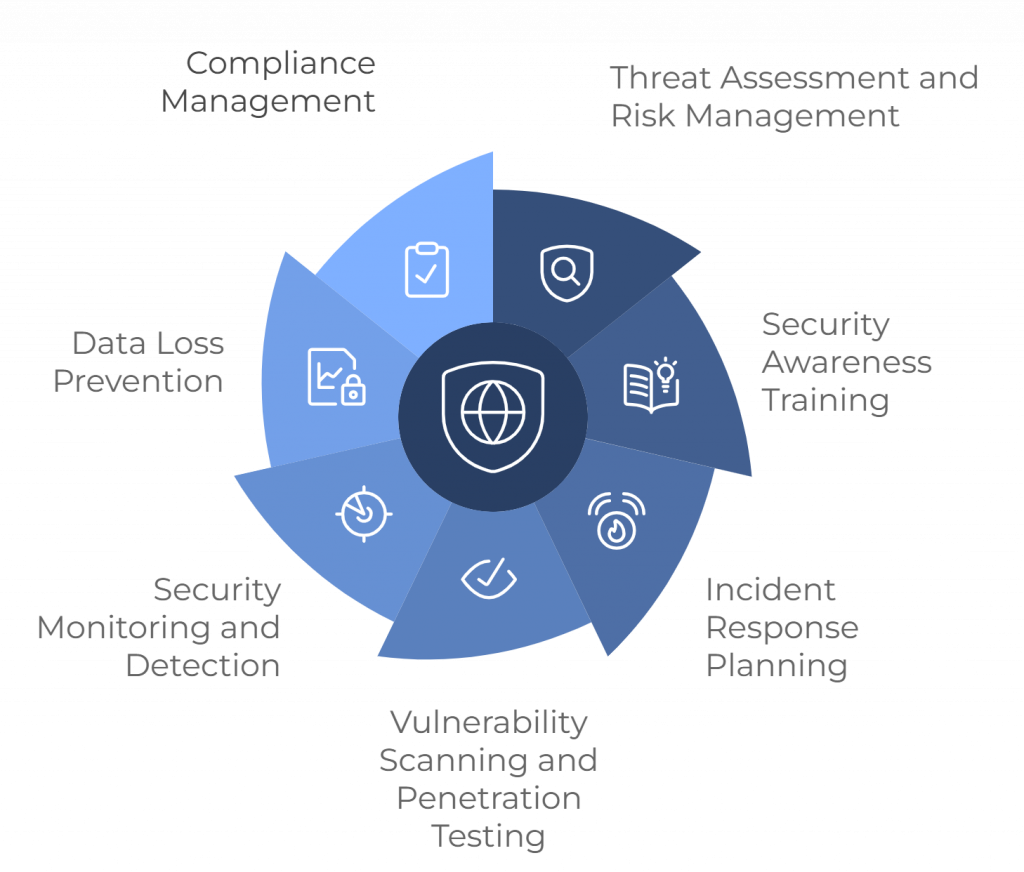
- Vulnerability Scanning and Penetration Testing: Using advanced tools, we identify and fix system vulnerabilities to strengthen your security posture.
- Security Monitoring and Detection: Continuous monitoring of your networks and systems allows us to quickly detect and respond to suspicious activity.
- Data Loss Prevention (DLP): We implement solutions to safeguard sensitive information, preventing accidental or intentional data breaches.
- Compliance Management: We help ensure adherence to industry standards and regulations like GDPR, HIPAA, and PCI DSS, keeping your business compliant and secure.
Why choose Experion’s ISaaS?
- Expertise and Experience: Our team of seasoned security professionals has extensive experience safeguarding organizations of all sizes.
- Tailored Solutions: We collaborate with you to fully understand your specific needs and deliver customized security solutions.
- Proactive Approach: We adopt a proactive stance, anticipating potential threats and implementing preventive strategies to protect your business.
- Scalability: Our ISaaS solutions can be easily scaled to meet your growing needs.
- Cost-Effective: Our managed security services provide comprehensive protection at a fraction of the cost of building and maintaining an in-house security team.
Conclusion
In conclusion, information security is a fundamental component of cybersecurity, essential for protecting sensitive data, maintaining system integrity, and ensuring the availability of information. By adopting robust security measures and staying vigilant against evolving threats, organizations can effectively safeguard their assets and reduce risks.
From threat detection to vulnerability management and compliance, Experion’s tailored services keep you ahead of evolving cyber threats. Trust our proven track record to safeguard your business so you can focus on what you do best. Secure your future; partner with us for top-tier cybersecurity solutions. Let’s connect today!

