In an era where digital transformation is reshaping every industry, Vulnerability Management has emerged as a cornerstone of successful business strategy. As companies increasingly rely on complex technologies and interconnected systems, the potential for vulnerabilities to disrupt operations and compromise data security grows exponentially. Leveraging Vulnerability Management effectively not only shields businesses from emerging threats but also serves as a catalyst for sustainable growth and competitive advantage. By systematically identifying and addressing weaknesses before they can be exploited, businesses can secure their operations and focus on driving innovation and growth.
In an era where digital transformation is reshaping every industry, Vulnerability Management has emerged as a cornerstone of successful business strategy. As companies increasingly rely on complex technologies and interconnected systems, the potential for vulnerabilities to disrupt operations and compromise data security grows exponentially. Leveraging Vulnerability Management effectively not only shields businesses from emerging threats but also serves as a catalyst for sustainable growth and competitive advantage. By systematically identifying and addressing weaknesses before they can be exploited, businesses can secure their operations and focus on driving innovation and growth.
For organizations looking to stay ahead of the curve, Vulnerability Management is more than a mere security measure—it’s a strategic asset. It empowers businesses to operate with confidence, knowing that their systems and data are safeguarded against potential threats. This proactive approach allows companies to respond swiftly to new challenges, enhance their operational efficiency, and build stronger relationships with customers and stakeholders.
In a landscape where cyber threats are becoming more sophisticated, an effective Vulnerability Management strategy is crucial for maintaining a competitive edge and unlocking new opportunities for advancement.
The Experion Approach
Experion adopts a Risk-Based Vulnerability Management (RBVM) approach rather than traditional vulnerability management methods.
RBVM is a strategic approach to cybersecurity that focuses on addressing vulnerabilities based on the potential risk they pose to an organization. Unlike traditional vulnerability management, which typically emphasizes identifying and patching vulnerabilities, RBVM takes a more comprehensive approach by considering key factors such as:
- Asset Criticality: The importance of an asset to the organization’s operations.
- Vulnerability Severity: The potential impact of a successful exploit.
- Threat Actor Activity: The likelihood that a vulnerability will be exploited.
By integrating these factors, RBVM enables organizations to concentrate their efforts on the vulnerabilities that present the greatest risk, thereby enhancing their security posture while optimizing their budget and time.
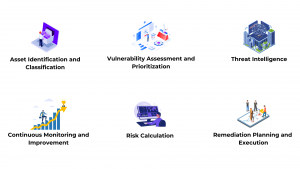
Key Components of RBVM
- Asset Identification and Classification: It is essential to identify and classify critical assets. This includes understanding the systems, applications, and data that are vital to business operations.
- Vulnerability Assessment and Prioritization: This step involves identifying vulnerabilities, evaluating their severity, and prioritizing them based on the potential impact on the organization.
- Threat Intelligence: Collecting information on potential threats and their tactics helps prioritize vulnerabilities that are most likely to be exploited.
- Risk Calculation: Organizations can calculate the overall risk associated with each vulnerability by combining asset criticality, vulnerability severity, and threat intelligence.
- Remediation Planning and Execution: Once vulnerabilities are prioritized, they are addressed through patching, configuration changes, or other mitigation strategies.
- Continuous Monitoring and Improvement: The RBVM process is ongoing, requiring regular risk reassessment and updates to the remediation plan.
Benefits of RBVM
- Enhanced Security Posture: By targeting high-risk vulnerabilities, organizations can significantly reduce their exposure to cyberattacks.
- Optimized Resource Allocation: RBVM helps organizations prioritize their security investments, ensuring resources are used efficiently.
- Reduced Risk of Data Breaches: Promptly addressing critical vulnerabilities minimizes the risk of data loss and financial damage.
- Regulatory Compliance: Many regulations require effective risk management, and RBVM supports meeting these compliance requirements.
Our Real-World Impact
Our client, an employee-owned engineering, procurement, consulting, and construction company with a 100-year legacy in sustainable infrastructure, faced significant challenges, including accumulated, unattended vulnerabilities, the need to improve security postures, and applications requiring federal compliance.
Experion partnered with the client to address these issues by establishing a perfect blend of automated and manual processes to identify and remediate vulnerabilities. Leveraging ITIL practices, Experion enhanced processes and patched new servers while implementing hardened practices such as TLS/SSL and CIS standards.
As a result, the client achieved a 70% reduction in vulnerabilities over one year, significantly improving the security posture of both cloud and on-premises systems. This success extended the project’s scope to include network vulnerabilities and endpoints, optimized patching cycles to cover third-party vulnerabilities, and fine-tuned scanner configurations to enhance performance and resolve sync issues with the ITSM tool, ensuring the recurrence of vulnerabilities was mitigated.
In Conclusion
At Experion Technologies, we go beyond traditional security measures to offer a comprehensive and proactive approach that integrates seamlessly into your business processes. Our commitment to excellence and innovation ensures that you are well-positioned to handle emerging threats and capitalize on new opportunities with confidence.
Are you ready to take your security strategy to the next level and unlock new growth potential?
Fill out the form below to connect with our experts and discover how our tailored Vulnerability Management solutions can transform your business.
Let us help you build a secure, resilient, and prosperous future—one that stands strong against any challenge.
Together, we can turn vulnerabilities into opportunities and propel your business to new heights.