At Experion, we believe that effective cybersecurity begins at the endpoints – the devices and systems that connect to your network. As businesses become more connected and remote work becomes the norm, the number of devices accessing corporate networks has increased exponentially, making end-point protection a critical aspect of any cybersecurity strategy. Our approach to end-point security focuses on ensuring that every device, whether it’s a laptop, smartphone, or IoT device, is equipped with the right defenses to safeguard your business from evolving cyber threats.
What is End-Point Protection?
End-point protection is a cybersecurity strategy designed to secure end-user devices from unauthorized access, malware, and data breaches. It involves deploying software and security protocols that monitor, detect, and respond to malicious activities targeting endpoints. Endpoints are often the first line of defense, serving as access points for sensitive business information. Thus, securing them is crucial to prevent potential vulnerabilities from becoming major security incidents.
Why is End-Point Protection Critical?
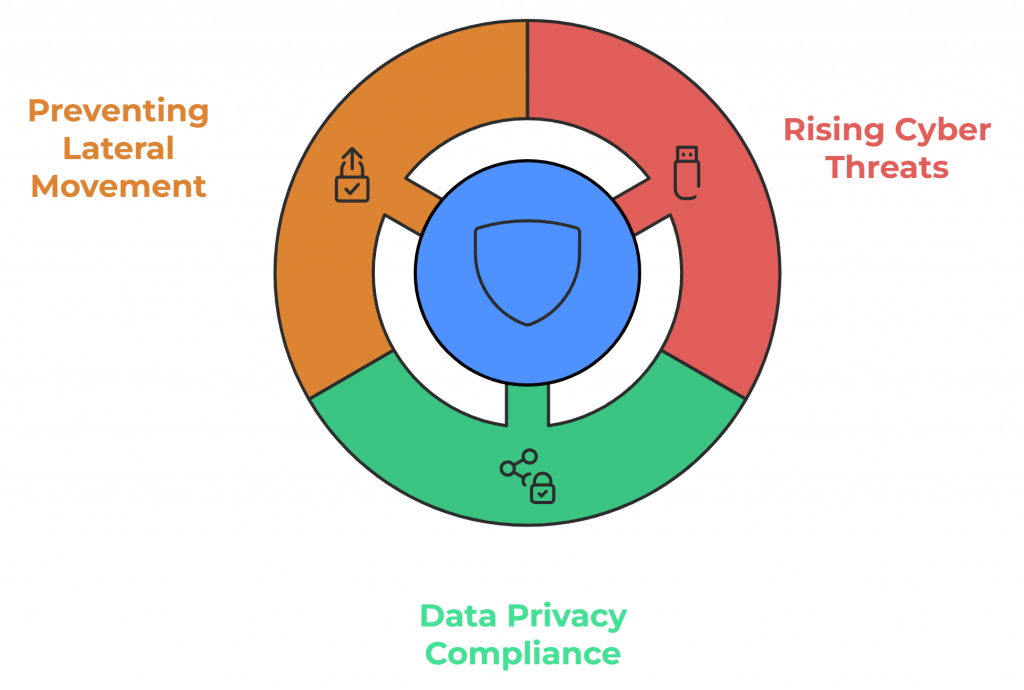
Rising Cyber Threats Targeting Endpoints
With the rise of remote work and BYOD (Bring Your Own Device) policies, businesses are more vulnerable to attacks targeting individual devices. Phishing, malware, and ransomware are just a few of the threats that can exploit unprotected endpoints to gain a foothold in corporate networks.
Data Privacy and Compliance
Many industries, such as healthcare,fintech and finance, have stringent data protection regulations. End-point protection helps ensure compliance by securing data at the device level, reducing the risk of breaches and maintaining the privacy of sensitive information.
Preventing Lateral Movement
Cyber attackers often start by compromising a single endpoint and then move laterally across the network to access high-value assets. Effective end-point protection stops this lateral movement, preventing a single device breach from escalating into a larger network compromise.
Key Features of Effective End-Point Protection
Advanced Threat Detection
Today’s cyber threats are highly sophisticated, capable of bypassing traditional antivirus software. Experion’s end-point protection solutions use advanced threat detection techniques such as machine learning, behavioral analysis, and AI to identify and block malicious activities in real-time. This proactive approach enables early detection of zero-day vulnerabilities and complex malware strains.
Device Control and Monitoring
End-point protection includes device control features to manage and monitor the use of external storage devices like USB drives. By setting permissions and restricting access, businesses can minimize the risk of unauthorized data transfers and potential data leaks.
Data Encryption
To ensure that sensitive data remains protected even if a device is lost or stolen, encryption is a critical component. End-point protection solutions encrypt data at rest and in transit, ensuring it remains secure and unreadable to unauthorized users—critical for businesses managing sensitive customer information or intellectual property.

Application Control
Not all applications are safe. Application control features allow IT teams to whitelist approved software and block untrusted or potentially harmful applications. This minimizes the risk of malware infections through unauthorized software downloads.
Threat Response and Remediation
Detection alone is not enough. Experion’s solutions offer automated and manual remediation options to quickly isolate compromised devices, remove threats, and restore systems to their pre-infected state, ensuring minimal disruption to business operations.
Integration with Endpoint Detection and Response (EDR)
For enhanced visibility and control, integrating end-point protection with Endpoint Detection and Response (EDR) capabilities is essential. EDR solutions provide deeper insights into security incidents, allowing security teams to perform thorough investigations and gain a better understanding of the threat landscape.
Experion’s End-Point Protection Strategy
At Experion, we take a holistic approach to end-point protection that goes beyond just deploying software. Our strategy involves a comprehensive assessment of your organization’s existing security posture, identifying potential gaps, and implementing robust solutions tailored to your unique needs. Here’s how we do it:
Assessment and Planning
We start by evaluating your current end-point environment and understanding the specific challenges your organization faces. This involves reviewing device types, operating systems, user roles, and data access patterns. Based on these insights, we develop a customized end-point protection strategy that aligns with your overall cybersecurity framework.
Deployment of Advanced Solutions
Using industry-leading tools and technologies, we deploy end-point protection solutions that include features such as multi-layered malware defense, AI-based threat detection, and data encryption. Our solutions are designed to work seamlessly across all devices, providing consistent protection without impacting performance.
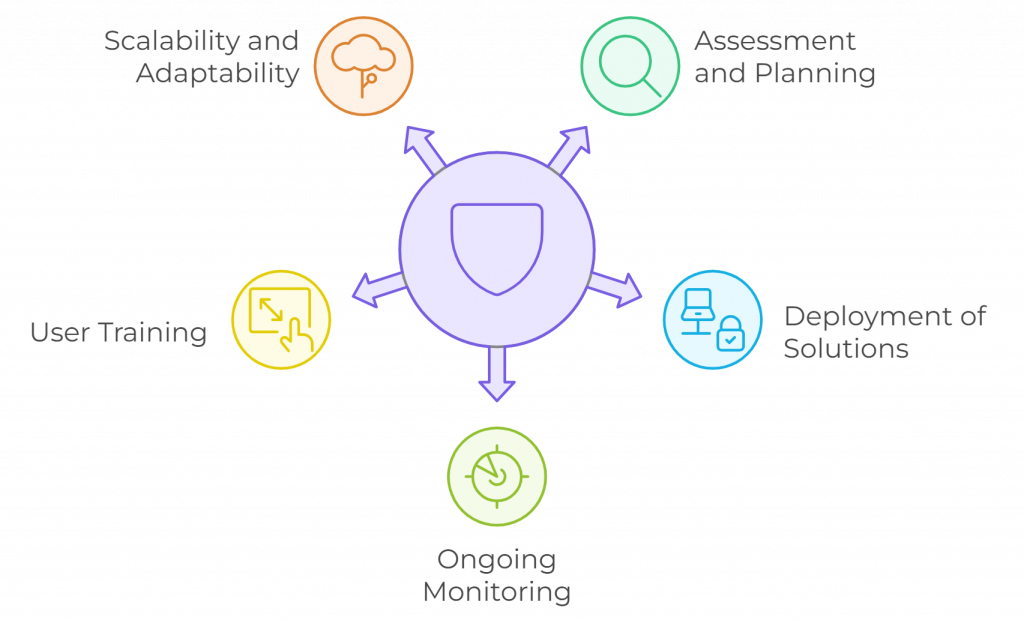
Ongoing Monitoring and Management
Effective end-point protection requires continuous monitoring and management. Our cybersecurity team provides round-the-clock monitoring, using analytics to identify unusual activity and respond promptly. We also conduct regular security reviews to ensure your defenses stay updated.
User Training and Awareness
Human error is often the weakest link in cybersecurity. To reinforce our end-point protection efforts, we provide user training and awareness programs that educate employees on best practices for maintaining device security. From recognizing phishing attempts to handling sensitive data, our training programs empower your workforce to become an active line of defense.
Scalability and Adaptability
As your business grows, so does your cybersecurity needs. Our solutions are scalable and adaptable, ensuring that new devices and users can be added easily. This flexibility makes our solutions ideal for dynamic environments where the endpoint landscape is constantly changing.
Safeguard Your Digital Perimeter with Experion
In an era of sophisticated cyber threats, end-point protection is not just an option – it’s a necessity. Experion’s tailored end-point protection solutions provide the comprehensive security your business needs to stay protected, compliant, and resilient. Contact us today to learn more about how we can secure your endpoints and strengthen your overall cybersecurity posture.

