At Experion Technologies, we help businesses build digital products that don’t just perform — they endure — by embedding trust and security into every layer of the web application.
Web applications are the lifeblood of today’s digital businesses. From eCommerce platforms and banking portals to enterprise dashboards and healthcare systems, they power customer experiences, transactions, and decision-making. Yet, as their reach and complexity grow, so do the risks.
According to Verizon’s Data Breach Investigations Report, 43% of all breaches are web application-related, with the average breach costing over $4.45 million.
Traditional firewalls and antivirus systems, though necessary, are no longer enough to defend against evolving cyber threats. Attackers exploit business logic flaws, weak APIs, and misconfigurations that go unnoticed in standard defenses.
That’s where Web Application Penetration Testing (WAPT) comes in — a proactive security assessment strategy designed to identify vulnerabilities before attackers do. It mimics real-world hacking scenarios to uncover and address potential weaknesses in your web ecosystem, strengthening both resilience and customer trust.
What is Web Application Penetration Testing?
Web Application Penetration Testing (often called web app pen testing) is a simulated cyberattack conducted on a web application to evaluate its security posture. The objective is to identify vulnerabilities in your applications — whether in the source code, server configuration, or user interface — that could be exploited by attackers.
It goes beyond routine security scans. While automated vulnerability assessment tools highlight potential flaws, penetration testing services validate and exploit them to assess the actual risk and impact. This combination provides organizations with actionable insights to strengthen their application security.
Difference Between Vulnerability Scanning and Penetration Testing
A vulnerability scan is like a diagnostic check — it detects possible issues through automated scripts. Penetration testing involves a trained professional attempting to exploit weaknesses, much like a real attacker, to assess how deep a breach could go.
Vulnerability scanning tells you what might be wrong; penetration testing of web application tells you what could happen if someone tried to exploit it.
Common Standards Followed
Professional web application penetration testing services adhere to globally recognized frameworks and standards, such as:
- OWASP (Open Web Application Security Project): The de facto guide for identifying and mitigating common web app risks.
- NIST SP 800-115: Defines a structured approach to information security testing.
- ISO 27001: Ensures compliance with information security management best practices.
Together, these standards ensure that every application security audit follows a repeatable, reliable, and compliance-ready methodology.
Importance of Penetration Testing for Web Application
Increasing Complexity of Web Ecosystems
Modern web ecosystems are a tangle of microservices, APIs, and third-party integrations hosted across multi-cloud environments. Each connection expands the attack surface.
Application penetration testing services ensure that as businesses scale their digital infrastructure, they don’t scale their vulnerabilities along with it.
Real-World Examples
Consider the 2023 MOVEit file transfer breach — a single vulnerability led to the compromise of data from hundreds of global organizations. Or the Marriott breach, where insufficient access control exposed millions of customer records. Many such incidents could have been prevented through web application penetration testing and regular security testing methodology updates.
Web App Security Compliance and Risk Management
Industries governed by regulations like GDPR, PCI DSS, and HIPAA require stringent protection of personal and financial data. Regular web application penetration testing not only ensures compliance but also safeguards your organization from fines, lawsuits, and loss of customer trust.
Financial and Reputational Impact of Ignoring Pen Testing
Ignoring penetration testing for web applications is like skipping insurance on your most valuable digital assets. Beyond financial losses, a single breach can erode customer confidence and brand reputation overnight. Proactive testing builds assurance — for your users, partners, and investors.
Web Application Penetration Testing Methodology: How It Works?
A robust web application security penetration testing process follows a systematic and ethical hacking methodology.
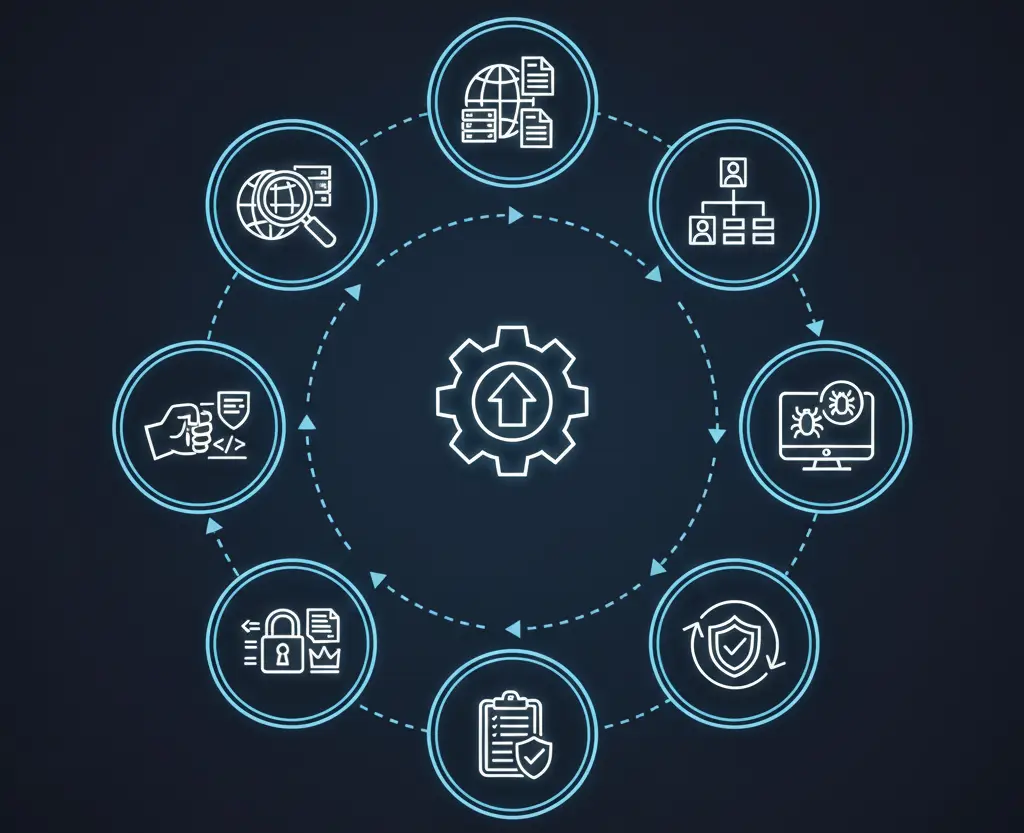
- Information Gathering:
The tester collects data about the target application, including domains, IPs, APIs, and backend frameworks. This stage maps the potential attack surface. - Threat Modeling:
Analysts identify assets, data flows, and threat vectors using frameworks like STRIDE or PASTA to simulate attacker behavior. - Vulnerability Analysis:
Through automated web application penetration testing tools like Burp Suite or OWASP ZAP and manual code review, vulnerabilities are detected. - Exploitation:
Ethical hackers safely exploit identified flaws — from SQL injections to misconfigurations — to determine the actual business impact. - Post-Exploitation:
Here, testers assess data exposure, privilege escalation, and lateral movement possibilities. - Reporting & Remediation:
Finally, a comprehensive report is delivered with vulnerability details, risk ratings, exploitation evidence, and prioritized remediation steps. - Re-Testing:
Once fixes are implemented, a re-test validates their effectiveness — closing the loop in the web app security testing lifecycle.
Common Web Application Vulnerabilities Uncovered During Penetration Testing
During a web application penetration test, several recurring vulnerabilities surface, including:

- SQL Injection (SQLi): Attackers manipulate database queries to access sensitive data.
- Cross-Site Scripting (XSS): Occurs when malicious scripts are injected into user-accessed web pages.
- Broken Authentication & Session Management: Poor session handling enables account hijacking.
- Insecure Direct Object References (IDOR): Unauthorized access to objects or data by altering parameters.
- Cross-Site Request Forgery (CSRF): Forces authenticated users to perform unwanted actions.
- Security Misconfigurations: Weak headers, default passwords, or exposed files.
- Sensitive Data Exposure: Inadequate encryption of financial or personal data.
At Experion Technologies, we combine automation with expert analysis to ensure such vulnerabilities are not just detected — they’re eliminated.
Types of Web Application Penetration Tests
- Black Box Testing
The tester has no prior knowledge of the system — mimicking an external attacker. It’s ideal for assessing real-world exposure.
- White Box Testing
The tester has full access to the source code and internal architecture, allowing a deeper dive into logic flaws and backend vulnerabilities.
- Gray Box Testing
A balanced approach where limited information is shared. It offers the realism of black box testing and the efficiency of white box testing.
Black box vs white box testing ultimately depends on your goals — whether you’re testing perimeter defenses or internal resilience.
- Automated vs Manual Penetration Testing
Automated tools ensure speed and coverage, while manual testing brings creativity and contextual judgment.
For most enterprises, a hybrid approach works best — automated web application penetration testing for breadth and manual testing for depth.
Best Web Application Penetration Testing Tools and Frameworks
Automated Tools
- Burp Suite: Comprehensive suite for crawling, scanning, and exploiting vulnerabilities.
- OWASP ZAP: Open-source tool for detecting web app flaws.
- Acunetix: Automates scanning for over 7,000 vulnerabilities.
- Netsparker: Known for accuracy in identifying false positives.
Manual Tools
- Nmap: Network mapping and discovery tool.
- Metasploit: Exploitation framework for advanced attack simulation.
- Nikto: Scans web servers for dangerous files and outdated components.
- SQLmap: Automates SQL injection detection and exploitation.
Importance of Combining Tools with Human Expertise
Even the best tools can miss logical vulnerabilities or context-specific risks. Pairing them with skilled ethical hackers ensures your web application penetration testing service covers every possible angle — from code to configuration to behavior.
Business Benefits of Penetration Testing

- Higher ROI through Prevention: A breach can cost millions; a web application penetration test is a fraction of that cost.
- Customer Trust & Brand Reputation: Secure applications inspire confidence.
- Regulatory Compliance: Meet OWASP penetration testing, GDPR, and PCI DSS standards.
- Operational Continuity: Avoid downtime caused by attacks.
- Enhanced Security Posture: Continuous learning from pen test insights strengthens long-term resilience.
By investing in penetration testing for web applications, organizations future-proof their growth while maintaining regulatory and reputational integrity.
How Often Should You Perform Web Application Penetration Testing?
Security isn’t a one-time event. Experts recommend conducting application penetration testing services:
- Quarterly, or
- After major code changes or infrastructure upgrades, and
- Before compliance audits or certifications.
In modern DevSecOps pipelines, continuous application security testing integrates penetration testing within the SDLC, allowing developers to address vulnerabilities before they reach production.
Selecting the Right Web Application Penetration Testing Services Provider
Key Factors to Evaluate
When selecting a vendor for web application penetration testing services, consider:
- Certified ethical hackers (CEH, OSCP, CISSP).
- Experience across industries and compliance frameworks.
- Clear, structured security testing methodology.
- Action-oriented reporting and remediation guidance.
Questions to Ask Before Hiring a Vendor
- Which frameworks (OWASP, NIST, ISO 27001) do you follow?
- Do you offer both automated and manual testing?
- What’s your approach to post-remediation verification?
- How do you handle sensitive data during testing?
Benefits of Engaging a Professional Penetration Testing Company
Partnering with an established cybersecurity firm ensures not only vulnerability discovery but also strategic defense building — from coding best practices to infrastructure hardening.
At Experion, our web application penetration testing aligns with global standards and client-specific objectives, ensuring every assessment translates into measurable business security gains.
Future of Web Application Penetration Testing
AI in Web Security and Automation Threat Detection
AI-powered tools are revolutionizing how security teams detect and predict threats. Machine learning models can now identify anomalous patterns faster than humans, enabling automated web application penetration testing at scale.
Shift-left Security in Development Cycles
The “Shift Left” movement emphasizes embedding security early in the development lifecycle — integrating testing within CI/CD pipelines rather than waiting for post-deployment assessments.
The Rise of Continuous Pen Testing and Red Teaming
Continuous testing environments, supported by red teaming simulations, allow organizations to maintain always-on security, adapting quickly to emerging threats.
Emerging Trends in Web Application Penetration Testing
- AI and Machine Learning in Security Testing: Predictive threat modeling and intelligent vulnerability scoring.
- API Security Testing: Ensuring the integrity of data exchange in connected applications.
- Cloud-Native Application Testing: Adapting testing frameworks for containerized and serverless environments.
- DevSecOps Integration: Continuous pen testing as part of agile release cycles.
- Mobile and Progressive Web Apps (PWA): Testing hybrid applications for platform-specific vulnerabilities.
As digital ecosystems evolve, penetration testing for web application environments will become a continuous, AI-augmented discipline — not an annual checkbox.
Conclusion
Web applications power the modern digital enterprise — but they also attract some of the most sophisticated attacks.
By investing in web application security penetration testing, organizations don’t just protect data — they preserve trust, continuity, and credibility.
Proactive defense through penetration testing of web application ecosystems is the smartest strategy for businesses that value resilience as much as innovation.
Schedule your web application penetration testing consultation or application security audit with Experion Technologies today to stay one step ahead of cyber threats.


